What Is an IP Blacklist?

An IP blacklist is a list of Internet Protocol addresses that have been identified as sources of malicious activity, spam, or other undesirable behavior on the internet. When an address is blacklisted, it means that it has been flagged by a security or anti-spam service as a potential threat, and measures are taken to restrict or block communication from that particular Internet Protocol address.
Table of Contents
some common reasons why an IP address might be blacklisted:

- Spamming:
- If an Internet Protocol address is associated with sending a large volume of unsolicited emails (spam), it may be added to email blacklists.
- Malware Distribution:
- Internet Protocol addresses involved in distributing malware, hosting malicious content, or participating in botnets can be blacklisted to prevent further spread of threats.
- Phishing Attacks:
- Internet Protocol addresses associated with phishing websites or activities designed to deceive individuals into disclosing sensitive information may be blacklisted.
- Denial-of-Service (DoS) Attacks:
- Internet Protocol addresses launching or participating in Denial-of-Service attacks, which aim to overwhelm a system or network, may be blacklisted to mitigate the impact.
- Suspicious Activity:
- Unusual or suspicious behavior, such as multiple failed login attempts or scanning for vulnerabilities, can lead to an Internet Protocol address being blacklisted.
- Botnet Participation:
- Internet Protocoladdresses that are part of a botnet, a network of compromised computers controlled by a malicious entity, may be blacklisted to disrupt the botnet’s activities.
- Violations of Terms of Service:
- Some online services and platforms maintain blacklists to block Internet Protocol addresses that violate their terms of service, such as engaging in abusive behavior or violating usage policies.
- Fraudulent Activities:
- Internet Protocoladdresses associated with fraudulent activities, such as online scams or identity theft, may be blacklisted to protect users.
Limitations of blacklists

Blacklists, while valuable tools in the cybersecurity arsenal, come with inherent limitations that can impact their effectiveness. One key challenge is the potential for false positives, where legitimate entities are incorrectly flagged as malicious. This can lead to service disruptions, inconvenience, and erode trust. Conversely, false negatives are also a concern, as dynamic threats may go undetected by static blacklists that struggle to keep pace with rapidly evolving cyber threats.
Another limitation arises from the static nature of blacklists. They may lack the agility to adapt quickly to emerging threats, such as zero-day exploits or evolving malware. Sophisticated malicious actors constantly employ evasion techniques, like changing Internet Protocol addresses or using proxies, to circumvent blacklists. The lack of contextual understanding is a significant constraint, as blacklists often focus on specific indicators of malicious activity without considering the broader behavior or tactics of attackers.
Moreover, blacklists often depend on historical data of known threats, making them less effective against previously unseen or emerging threats. This limitation underscores the need for a more comprehensive security strategy that integrates blacklists with other measures such as behavior analysis, anomaly detection, threat intelligence feeds, and real-time monitoring. A multi-layered approach helps mitigate the shortcomings of blacklists and enhances overall cybersecurity resilience.
The Importance of IP Addresses

IP addresses (Internet Protocol addresses) play a crucial role in computer networking and communication on the Internet. Their importance stems from various functions and capabilities they provide in the digital realm. Here are several key aspects highlighting the importance of IP addresses:
- Device Identification:
- The uniquely identify devices on a network, such as computers, servers, routers, and other networked devices. This identification is essential for data transmission and routing.
- Location Addressing:
- IP serve as location addresses in the network. They help route data from the source device to the destination device across the complex network infrastructure of the Internet.
- Communication and Data Routing:
- IP addresses are used to route data packets between devices on a network. They enable efficient communication by specifying the source and destination of data, allowing routers to determine the optimal path for data transmission.
- Internet Accessibility:
- IP addresses are crucial for accessing resources on the Internet. Every website, server, or online service has a unique IP address. Domain Name System (DNS) translates human-readable domain names into IP addresses, making it easier for users to access websites without memorizing numerical addresses.
- Subnetting and Network Segmentation:
- IP addresses are organized into subnets, allowing for the segmentation of large networks into smaller, manageable parts. This helps in optimizing network performance, security, and management.
- Network Troubleshooting:
- IP addresses are essential for network troubleshooting. Network administrators use tools to trace the route of data packets and diagnose connectivity issues by analyzing the IP addresses involved.
- Security and Access Control:
- IP addresses are used in security measures and access control mechanisms. Firewalls, for example, can filter and control network traffic based on IP addresses, helping to protect against unauthorized access and potential threats.
- Device Configuration:
- IP addresses are used in configuring devices on a network. Devices need unique IP addresses to communicate properly, and network administrators assign and configure these addresses to ensure smooth operation.
- Quality of Service (QoS) Management:
- IP addresses are used to implement Quality of Service policies in networks. This allows administrators to prioritize certain types of traffic, ensuring that critical data, such as voice or video, gets higher priority for smoother transmission.
- Internet Protocol Versioning:
- There are two main versions of the Internet Protocol in use today: IPv4 and IPv6. IP addresses are critical in supporting the transition from IPv4 to IPv6, as the latter provides a larger address space to accommodate the growing number of devices connected to the Internet.
How Can You Tell If an IP Address Is Blocked?
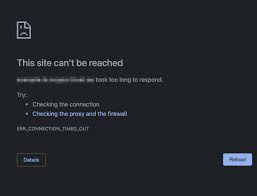
Determining whether an IP address is blocked involves several diagnostic methods. One common approach is to use network utilities like the ping and traceroute commands. A failed ping test, where requests consistently time out, or anomalies in traceroute results can indicate a potential blockage. Additionally, attempting to access a web server associated with the IP address through a web browser may reveal connectivity issues or error messages.
Checking firewall logs, if accessible, provides insights into any IP address-based blocks. Network administrators often rely on these logs to monitor and control incoming and outgoing traffic. Online tools, such as MXToolBox or WhatIsMyIPAddress, offer blacklist checks to see if an IP address is listed on known blacklists.
Communication issues, particularly in the context of email, can be indicative of IP blocks. Reviewing bounceback messages or error codes received when attempting to send emails may offer clues about the blocking reason.
For a more detailed analysis, network scanning tools like Nmap can be employed to identify open ports and services on the target system. Closed or filtered ports may suggest IP address blocking.
If suspicion arises about being blocked on a specific network or service, reaching out to the network administrator or support team is a proactive step. They can confirm whether the IP address is indeed blocked and provide information on the cause. However, it’s crucial to always ensure proper authorization before conducting any tests, especially on systems or networks that you do not own or administer, to avoid violating terms of service or legal regulations.