What is SSH

SSH, which stands for Secure Shell, is a cryptographic network protocol used for secure communication and data exchange between two computers over an unsecured network. It provides a secure way to access and manage remote systems, typically using a command-line interface. SSH is widely used for securely connecting to and managing servers, especially in the context of Unix-like operating systems.
Table of Contents
Here are key aspects of SSH:
- Authentication:
- SSH uses a combination of public-key cryptography, password authentication, or other methods to authenticate users. Public-key authentication is a common and secure method, involving a pair of public and private keys.
- Encryption:
- All communication between the client and server is encrypted to ensure confidentiality and prevent eavesdropping. This encryption covers the login process, commands sent to the remote system, and the output returned.
- Security Features:
- SSH provides a secure alternative to older, less secure protocols like Telnet and FTP. It protects against various security threats, including password sniffing, session hijacking, and man-in-the-middle attacks.
- Port Number:
- The default port for SSH is 22. However, this can be changed for security reasons if needed.
- Key Components:
- SSH is composed of two main components: the SSH client and the SSH server. The client is used to connect to a remote system, while the server runs on the remote system and allows incoming SSH connections.
- Use Cases:
- SSH is commonly used by system administrators, developers, and anyone who needs secure access to remote systems for tasks such as executing commands, managing files, and configuring settings.
- Tunneling:
- SSH supports tunneling, allowing users to create secure channels for other protocols, such as transferring files (SFTP), accessing web applications, and more.
- Versions:
- Secure Shell has multiple versions, with SSHv2 being the most widely used and recommended. It has various improvements over the earlier Secure Shellv1, including enhanced security features.
In summary, SSH is a crucial tool for securely connecting to and managing remote systems. Its encryption and authentication mechanisms make it a reliable and widely adopted protocol for secure communication over networks like the internet.
What is SSL
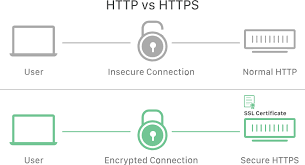
SSL, or Secure Sockets Layer, is a cryptographic protocol designed to provide secure communication over a computer network, particularly the internet. SSL is now deprecated and has been succeeded by its successor, TLS (Transport Layer Security). However, the term “SSL” is still commonly used to refer to the more modern versions of the protocol, such as TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3.
Here are key aspects of SSL/TLS:
- Purpose:
- SSL/TLS is primarily used to secure the transmission of sensitive information between a client (such as a web browser) and a server. It ensures that data exchanged between the two parties is encrypted and remains confidential.
- Authentication:
- SSL/TLS uses digital certificates to authenticate the identity of the server. This helps ensure that the client is connecting to the intended and legitimate server.
- Encryption:
- SSL/TLS encrypts the data transmitted between the client and the server, preventing eavesdropping and unauthorized access to sensitive information. The encryption ensures the confidentiality and integrity of the data.
- Handshake Process:
- When a client connects to a server using SSL/TLS, a handshake process occurs. This involves the exchange of cryptographic parameters, verification of the server’s digital certificate, and the generation of shared keys for secure communication.
- Port Number:
- The default port for secure communication using SSL/TLS is 443. This is commonly used in URLs with “https://” to indicate a secure connection, as opposed to the unencrypted “http://”.
- Versions:
- SSL had several versions, including SSLv2 and SSLv3. However, due to vulnerabilities in these versions, they are largely deprecated. TLS versions (TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3) have succeeded SSL, with TLS 1.3 being the latest and most secure version.
- Use Cases:
- SSL/TLS is widely used to secure data transmission on the internet, particularly in applications such as web browsing, online banking, email communication, and any other scenario where privacy and data integrity are critical.
- HTTPS (HTTP Secure):
- SSL/TLS is commonly implemented in conjunction with HTTP to create HTTPS, a secure version of the HTTP protocol. Websites that use HTTPS encrypt the data exchanged between the user’s browser and the web server.
In summary, SSL/TLS is a critical technology for securing communication on the internet. It provides encryption, authentication, and data integrity, making it essential for protecting sensitive information exchanged between clients and servers.
SSH vs SSL : The key difference

SSH (Secure Shell) and SSL (Secure Sockets Layer) are both cryptographic protocols designed to provide secure communication, but they serve different purposes and are used in distinct contexts. Here are the key differences between SSH and SSL:
- Purpose and Usage:
- SSH: Primarily used for secure remote access to systems and secure file transfers between machines. It provides a secure command-line interface for managing and accessing remote systems.
- SSL: Used for securing data transmission between applications over a network, particularly on the internet. It is commonly employed in web browsing, email, and other applications where data integrity and confidentiality are crucial.
- Authentication:
- SSH: Relies on public-key cryptography for authentication, although it can also use passwords or other methods. Public-key authentication is a common and secure method.
- SSL: Uses digital certificates for authentication. Both the server and, optionally, the client are authenticated using digital certificates.
- Encryption:
- SSH: Encrypts the entire communication session, providing confidentiality and integrity for the data being transmitted.
- SSL: Encrypts the data being transmitted between the client and the server. This ensures that even if intercepted, the data remains confidential.
- Port Number:
- SSH: The default port for Secure Shell is 22.
- SSL: The default port for HTTPS (HTTP over SSL/TLS) is 443. SSL can be used with other protocols, each having its own default port.
- Typical Use Cases:
- SSH: Commonly used by system administrators, developers, and anyone who needs secure command-line access to remote systems.
- SSL: Widely used in securing web traffic (HTTPS), email communication (SMTPS, POP3S, IMAPS), and other applications where secure data transmission is essential.
- Applications:
- SSH: Used for secure shell access, secure file transfers (SFTP), and secure tunneling.
- SSL: Applied in various applications like securing websites, online banking, e-commerce transactions, and any scenario where encrypted communication is required.
- Protocol Versions:
- Secure Shell : Has versions like SSHv1 and SSHv2. SSHv2 is the more modern and secure version.
- SSL: SSL has been largely deprecated in favor of its successor, TLS (Transport Layer Security). Modern implementations use TLS versions such as TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3.
Conclusion

In conclusion, Secure Shell and SSL (Secure Sockets Layer) are both cryptographic protocols that provide secure communication over networks, but they are used for different purposes. Secure Shell is primarily designed for secure remote access and file transfers, commonly used in system administration and development scenarios. On the other hand, SSL (or its successor TLS) is employed to secure data transmission between applications over the internet, with HTTPS being a prominent example in web browsing.
The key differences lie in their intended use cases, authentication methods, encryption approaches, default port numbers, and the types of applications they secure. Secure Shell focuses on secure command-line access and file transfers with authentication using methods like public-key cryptography, while SSL/TLS secures data transmission in various applications using digital certificates for authentication.
Understanding these distinctions is essential for choosing the appropriate protocol based on the specific security requirements of a given scenario, whether it involves secure remote management of systems (Secure Shell) or securing data exchanged over the internet (SSL/TLS).